We continue talking about IPv6, today we will discuss ICMPv6, we will do some tests to follow step by step how this protocol of control messages works in IPV6, we will take boot captures in both Windows and Linux, we will use Wireshark for boot captures and We will use virtual machines to make things easier for us. We will do some tests to follow step by step how this protocol of control messages works inside IPV6 For the analysis of use of ICMPv6, 2 virtual machines will be used, with the windows and linux operating system installed respectively, and the traffic captured at the start of the machines will be analyzed and some ping tests will be performed to analyze their respective traffic.
Linux boot capture:
As you know VMware by default creates 2 virtual networks, one in NAT mode that is nothing more than a software virtual interface that works in switch mode, where you can connect a multitude of virtual machines that will make NAT with your physical network interface, the ethernet the local machine. In this sense, I capture traffic from wireshark and configure the options of wireshark interface in Vmnet8 (virtual network).
Before explaining traffic it is convenient to ask yourself this question: What is ICMPv6 for? The purpose of this protocol is to allow each IPv6 router to discover the presence of multicast listeners on their directly connected links and to determine specifically which multicast addresses are of interest to the nodes.
Then after verifying that the virtual network exists, we proceed to capture the traffic on wireshark
Capture->start and after this we started the Linux virtual machine, the following was captured.
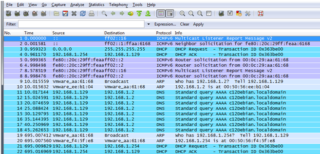
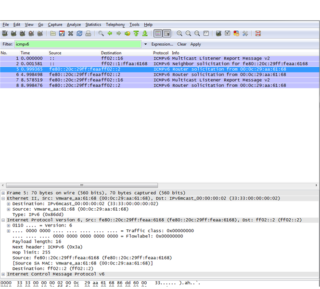
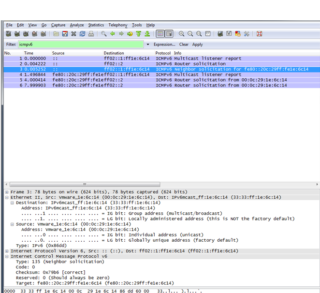
To search ICMPv6 we made a traffic filter with this type, we only put in the "Filter" field ICMPv6:
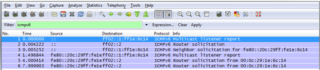
6 messages are seen in the following order:
1.- Multicast Listener Report Message V2.
2.- Neighbor solicitation.
3.- Router Solicitation.
4.- Multicast Listener Report Message v2.
5.- Router Solicitation.
Let's explain one by one:
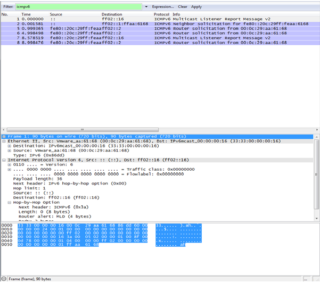
First Message: "Multicast Listener Report Message v2"
In the type field of ICMPv6 it has 8 bits and type 143 belongs to Multicast Listener Report Message v2:
Type: 143
RFC: 3810
These messages are sent to all the nodes to report (to neighboring routers) the current status of the multicast listeners or to change the state of the multicast listeners, or their interfaces.
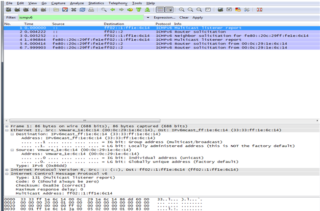
Second Message: "Neighbor Solicitation"
Possibly, the most important additions to the neighbor discovery protocol are the functions that formalize the exchange of parameters and the methods to determine the existence of neighboring hosts. These tasks include the new address resolution method in IPv6, as well as the next hop determination and neighbor inaccessibility detection processes. They require the use of two ICMPv6 messages: the Neighbor Solicitation and the Neighbor Advertisement message.
The Neighbor Solicitation message allows a device to verify that a neighbor exists and is accessible, and to initiate resolution of addresses. The Neighbor Advertisement message confirms the existence of a host or router, and also provides the address information layer when necessary. As you can see, these two messages are comparable to router advertisements and router request messages, but are used differently and include different parameters. Message Type: 135, RFC: 2461.
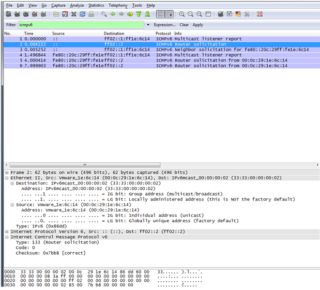
Third Message: "Router Solicitation"
Field Message Type ICMPv6: 133, RFC: 2461.
The hosts send this type of message to ask the routers to generate Router Advertisements or Router Warnings quickly.
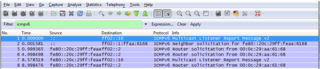
Windows boot capture:
The same capture procedure that was done previously with the Linux virtual machine was followed. Wireshark was configured with the Vmnet8 interface and proceeded to boot the Windows virtual machine and the following traffic was captured:
Interestingly, some differences can be verified at first sight regarding the sequence of neighbor discovery with respect to Linux and the use of ICMPv6 message types.
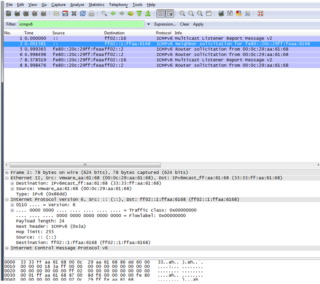
First Message: "Multicast Listener Report".
Sent by a host when joining a multicast group, or in response to the query multicast listener MLD sent by a router. RFC 2710, Value in the type field of ICMPv6 131.
Second Message: "Router Solicitation".
Field Message Type ICMPv6: 133, RFC: 2461.
The hosts send this type of message to ask the routers to generate Router Advertisements or Router Warnings quickly.
Third Message: "Neighbor Solicitation":
Neighbors request is explained in the Linux capture we can see that it is very similar protocols in different operating systems. If you have any questions, do not hesitate to comment on the entry and we do a feedback on this great protocol. See you next time ;)